How “Security Maturity” Affects an Organization’s Risk of a Potential Breach
The increase in security breaches over the past few years has every business — large and small — thinking about its current security levels and how to improve.
For companies, traditional defense – for example, quickly applying software patches and using technologies to block or identify malware infections – is just not enough. Despite how many resources you consume in an attempt to keep malware and other threats out, all can be undone as soon as an unsuspecting user clicks on a malicious link or falls for a phishing attack, or a breach is exploited before it can be patched. Or any one of a multitude of other ways attackers can enter with one action. As we saw with Marriott, failing to rapidly react at the initial breach can cost the entire organization dearly.
The difference between the most secure organizations and the rest? They’re the ones that make cybersecurity a part of their overall culture – not do the bare minimum.
The table below outlines how corporate mindset and the perceived importance of security at the executive level affects an organization’s priorities when it comes to taking effective measures to manage cyber risks and threats.
The companies run by leaders and corporate board members with advanced “security maturity” are focusing on breach prevention AND intrusion detection and response. They’re constantly testing their own networks for weaknesses, and regularly drilling their breach response preparedness. These organizations are also coming up with inventive ways to reduce the amount of sensitive data that they store and protect.
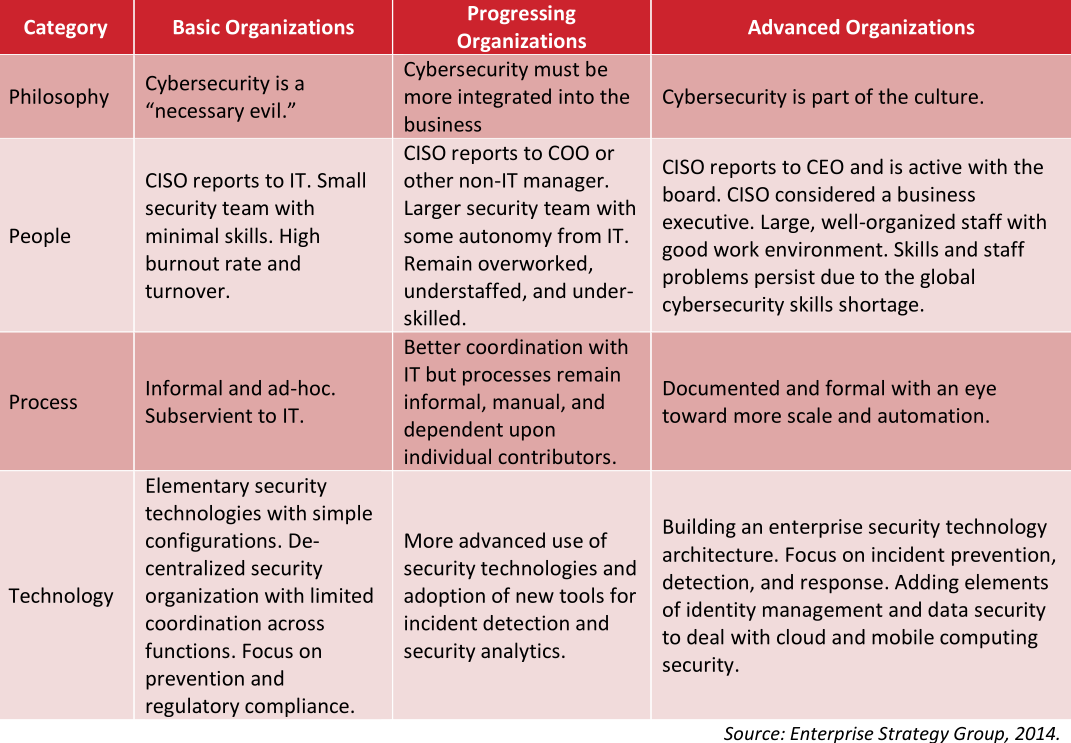
But the “security maturity” table doesn’t just show how some organizations are lacking. It can serve as a very basic roadmap for organizations that wish to change. Companies that are able to advance in maturity have a leadership that is both invested and interested in making security a fundamental priority. The key to success is influencing leadership to make security a priority before the organization falls victim to a breach.
What is the “security maturity” level of your organization?




